
In an increasingly digital world, the security of your applications is paramount to safeguarding your organization’s valuable assets. With cyber threats becoming more sophisticated every day, mastering application security monitoring has never been more critical. This proactive approach not only defends against potential breaches but also enhances your overall security posture. From identifying vulnerabilities before they can be exploited to ensuring compliance with industry standards, strategic monitoring can be your first line of defense. In this article, we’ll explore essential strategies that will equip you to protect your digital assets effectively. Dive in to learn how you can establish a robust application security monitoring framework, enabling you to stay ahead of threats and maintain the trust of your users. Don’t leave your applications vulnerable; take charge of your security today!
Understanding Application Security Monitoring
Application security monitoring is a critical practice in the modern cybersecurity landscape, designed to ensure that applications are protected against potential threats and vulnerabilities. This process involves continuously tracking and analyzing application behavior, detecting unusual activities, and responding to potential security incidents promptly. The goal is to identify and mitigate risks before they can be exploited by malicious actors.
A comprehensive application security monitoring strategy typically includes various components, such as real-time user monitoring, log analysis, and threat intelligence. These elements work together to provide a holistic view of the application’s security posture. By leveraging these tools and techniques, organizations can gain valuable insights into their security environment, enabling them to address vulnerabilities proactively and maintain the integrity of their digital assets.
In addition to protecting against immediate threats, effective application security monitoring also helps organizations comply with industry regulations and standards. As cyber threats continue to evolve, staying ahead of these risks requires a proactive and adaptive approach. By implementing robust security monitoring practices, organizations can safeguard their applications, protect sensitive data, and build trust with their users.
The Importance of Application Security in Today’s Digital Landscape
In today’s interconnected world, applications play a pivotal role in the operations of businesses and organizations. They facilitate communication, streamline processes, and provide critical services to users. However, the increasing reliance on digital applications also brings with it a heightened risk of cyber threats. Cybercriminals are constantly devising new methods to exploit vulnerabilities in applications, making it imperative for organizations to prioritize application security.
The consequences of a security breach can be severe, ranging from financial losses to reputational damage. A single security incident can compromise sensitive data, disrupt business operations, and erode customer trust. As a result, organizations must invest in robust security measures to protect their applications from potential threats. Application security monitoring is a key component of this strategy, providing the visibility and insights needed to detect and respond to security incidents in real-time.
Moreover, the regulatory landscape is becoming increasingly stringent, with governments and industry bodies imposing strict requirements on data protection and cybersecurity. Organizations that fail to comply with these regulations may face significant fines and legal repercussions. By implementing effective application security monitoring practices, organizations can not only protect their digital assets but also ensure compliance with relevant laws and standards.
Key Components of Effective Application Security Monitoring
Effective application security monitoring encompasses several key components that work together to provide comprehensive protection. These components include real-time monitoring, log analysis, threat intelligence, and incident response.
Real-time monitoring involves continuously tracking application behavior to detect any unusual or suspicious activities. This proactive approach enables organizations to identify and respond to potential threats before they can cause significant damage. By leveraging advanced monitoring tools, organizations can gain real-time visibility into their applications and take immediate action to mitigate risks.
Log analysis is another critical component of application security monitoring. It involves collecting and analyzing logs generated by applications to identify patterns and anomalies that may indicate security issues. By examining these logs, organizations can gain valuable insights into their security environment and detect potential threats early. Log analysis also helps in forensic investigations, allowing organizations to understand the root cause of security incidents and take corrective measures.
Threat intelligence involves gathering and analyzing information about potential threats and vulnerabilities. This information can come from various sources, such as security research, threat feeds, and community forums. By staying informed about the latest threats and attack vectors, organizations can proactively address vulnerabilities and strengthen their security posture. Integrating threat intelligence into the application security monitoring process enables organizations to stay ahead of emerging threats and protect their digital assets effectively.
Incident response is the final component of effective application security monitoring. It involves having a well-defined plan in place to respond to security incidents promptly. This plan should include steps for detecting, containing, and mitigating the impact of security breaches. By having a robust incident response strategy, organizations can minimize the damage caused by security incidents and recover quickly.
Common Threats to Application Security
Understanding the common threats to application security is essential for developing effective monitoring strategies. Cyber threats are constantly evolving, and staying informed about the latest attack vectors can help organizations better protect their applications. Some of the most common threats to application security include SQL injection, cross-site scripting (XSS), and distributed denial of service (DDoS) attacks.
SQL injection is a type of attack that exploits vulnerabilities in an application’s database layer. By injecting malicious SQL statements into an application’s input fields, attackers can gain unauthorized access to sensitive data, manipulate database contents, and even execute arbitrary commands. SQL injection attacks can have severe consequences, including data breaches and system compromise. Organizations must implement proper input validation and parameterized queries to protect against SQL injection.
Cross-site scripting (XSS) is another prevalent threat to application security. XSS attacks occur when attackers inject malicious scripts into web pages viewed by other users. These scripts can steal user credentials, perform unauthorized actions on behalf of the user, and spread malware. XSS vulnerabilities typically arise from inadequate input validation and output encoding. To prevent XSS attacks, organizations should implement robust input validation, sanitize user inputs, and use content security policies.
Distributed denial of service (DDoS) attacks involve overwhelming a target application with a flood of traffic, rendering it unavailable to legitimate users. DDoS attacks can disrupt business operations, cause financial losses, and damage an organization’s reputation. Attackers often use botnets to launch large-scale DDoS attacks, making them difficult to mitigate. Organizations can protect against DDoS attacks by implementing traffic filtering, rate limiting, and leveraging DDoS protection services.
Best Practices for Implementing Application Security Monitoring
Implementing effective application security monitoring requires a combination of best practices and strategies. By following these guidelines, organizations can enhance their security posture and protect their digital assets from potential threats. Some of the best practices for implementing application security monitoring include defining clear objectives, establishing a baseline, and continuously updating monitoring tools and techniques.
Defining clear objectives is crucial for the success of any security monitoring program. Organizations should identify their specific security goals, such as detecting unauthorized access, preventing data breaches, and ensuring compliance with regulations. By setting clear objectives, organizations can prioritize their monitoring efforts and allocate resources effectively.
Establishing a baseline is another important best practice. A baseline represents the normal behavior and performance of an application under typical conditions. By establishing a baseline, organizations can identify deviations from the norm that may indicate potential security issues. Regularly updating the baseline to reflect changes in the application environment is essential for accurate monitoring.
Continuously updating monitoring tools and techniques is critical for staying ahead of evolving threats. Cyber threats are constantly changing, and outdated monitoring tools may not be effective against new attack vectors. Organizations should regularly evaluate their monitoring tools, incorporate the latest threat intelligence, and adopt new technologies to enhance their security monitoring capabilities. Staying informed about emerging threats and industry best practices is essential for maintaining a robust security posture.
Tools and Technologies for Application Security Monitoring
There are numerous tools and technologies available to assist organizations in implementing effective application security monitoring. These tools provide real-time visibility into application behavior, detect potential threats, and enable organizations to respond promptly to security incidents. Some of the most widely used tools and technologies for application security monitoring include Security Information and Event Management (SIEM) systems, Web Application Firewalls (WAFs), and Intrusion Detection and Prevention Systems (IDPS).
Security Information and Event Management (SIEM) systems are comprehensive solutions that collect, analyze, and correlate security data from various sources. SIEM systems provide real-time monitoring, log analysis, and threat detection capabilities. By centralizing security data and applying advanced analytics, SIEM systems help organizations identify and respond to security incidents effectively. They also support compliance reporting and forensic investigations.
Web Application Firewalls (WAFs) are specialized security solutions designed to protect web applications from common threats, such as SQL injection and XSS attacks. WAFs monitor incoming and outgoing traffic, filtering out malicious requests and blocking potential attacks. By implementing a WAF, organizations can add an additional layer of protection to their web applications and mitigate the risk of security breaches.
Intrusion Detection and Prevention Systems (IDPS) are essential for detecting and preventing unauthorized access to applications and networks. IDPS solutions monitor network traffic and application behavior for signs of suspicious activities. They can detect potential threats, such as malware, DDoS attacks, and unauthorized access attempts. By deploying IDPS, organizations can enhance their security monitoring capabilities and protect their digital assets from a wide range of threats.
Integrating Application Security Monitoring into Your DevOps Pipeline
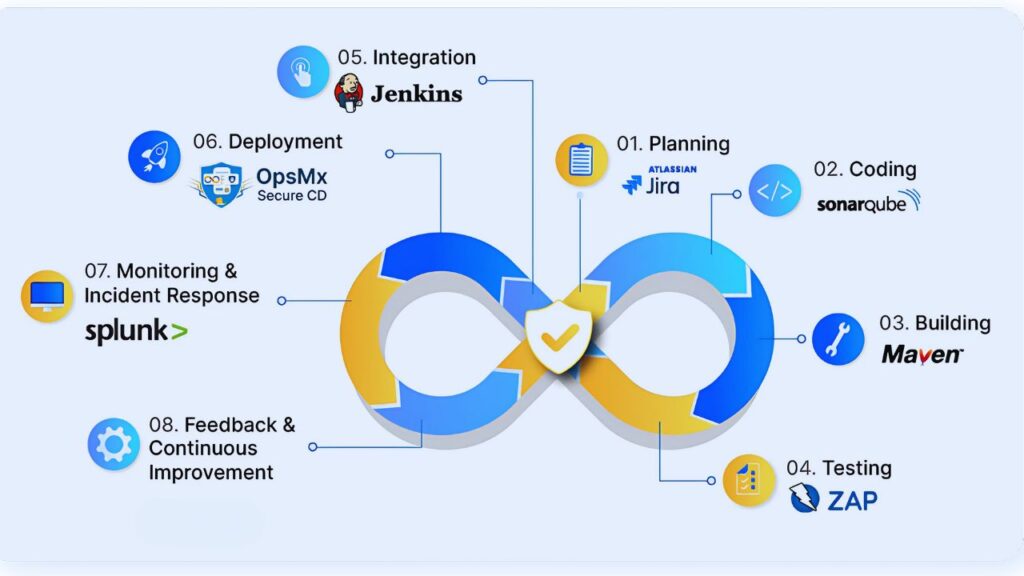
Integrating application security monitoring into the DevOps pipeline is a critical step in ensuring the security of applications throughout their lifecycle. DevOps practices emphasize continuous integration and continuous delivery (CI/CD), which can introduce security risks if not properly managed. By incorporating security monitoring into the DevOps pipeline, organizations can identify and address security issues early in the development process, ensuring that security is an integral part of the application lifecycle.
One of the key strategies for integrating security monitoring into the DevOps pipeline is to implement automated security testing. Automated security testing tools can be integrated into the CI/CD pipeline to perform regular security assessments of the application code. These tools can detect vulnerabilities, such as insecure coding practices and potential security flaws, before the code is deployed to production. By identifying and addressing security issues early, organizations can reduce the risk of security breaches and ensure the delivery of secure applications.
Another important aspect of integrating security monitoring into the DevOps pipeline is to foster a culture of collaboration between development, operations, and security teams. Security should be seen as a shared responsibility, with all team members working together to identify and mitigate security risks. This can be achieved through regular security training, collaboration tools, and clear communication channels. By promoting a security-first mindset, organizations can ensure that security is integrated into every stage of the application lifecycle.
Continuous monitoring and feedback loops are also essential for integrating security into the DevOps pipeline. Organizations should implement real-time monitoring tools to track application behavior and detect potential security issues during the development and deployment stages. Feedback loops should be established to provide timely feedback to development teams, enabling them to address security issues promptly. By continuously monitoring and improving security practices, organizations can enhance their security posture and deliver secure applications.
Case Studies: Successful Application Security Monitoring Implementations
Examining real-world case studies of successful application security monitoring implementations can provide valuable insights and lessons for organizations looking to enhance their security practices. These case studies highlight the challenges faced by organizations, the strategies they employed, and the outcomes they achieved. By learning from these examples, organizations can gain a better understanding of how to implement effective security monitoring practices.
One notable case study involves a large financial institution that faced significant security challenges due to the complexity of its application environment. The organization implemented a comprehensive application security monitoring strategy, including real-time monitoring, log analysis, and threat intelligence. By leveraging SIEM systems and WAFs, the organization was able to detect and respond to potential threats promptly. The implementation of automated security testing in the DevOps pipeline also helped identify and address security issues early in the development process. As a result, the organization significantly reduced the risk of security breaches and ensured compliance with industry regulations.
Another case study involves a healthcare organization that faced the challenge of protecting sensitive patient data from cyber threats. The organization implemented a multi-layered security monitoring approach, including IDPS, WAFs, and continuous monitoring tools. They also integrated security monitoring into their DevOps pipeline, enabling them to identify and address security issues during the development and deployment stages. By fostering a culture of collaboration between development, operations, and security teams, the organization was able to enhance its security posture and protect patient data effectively.
A third case study involves an e-commerce company that experienced a DDoS attack that disrupted its online services. The organization implemented a robust DDoS protection strategy, including traffic filtering, rate limiting, and leveraging DDoS protection services. They also implemented real-time monitoring tools to detect and respond to potential DDoS attacks promptly. By continuously updating their security monitoring tools and techniques, the organization was able to mitigate the risk of DDoS attacks and ensure the availability of its online services.
Measuring the Effectiveness of Your Application Security Monitoring
Measuring the effectiveness of application security monitoring is essential for ensuring that security practices are achieving their intended goals. By evaluating the performance of security monitoring tools and techniques, organizations can identify areas for improvement and make informed decisions about their security strategies. Some key metrics and methods for measuring the effectiveness of application security monitoring include incident detection rates, mean time to detect (MTTD), and mean time to respond (MTTR).
Incident detection rates measure the percentage of security incidents that are successfully detected by monitoring tools. A high incident detection rate indicates that monitoring tools are effective in identifying potential threats. Organizations should regularly review and analyze incident detection rates to ensure that monitoring tools are performing as expected. If incident detection rates are low, organizations may need to update their monitoring tools, incorporate additional threat intelligence, or adjust their monitoring strategies.
Mean time to detect (MTTD) measures the average time it takes to detect a security incident from the moment it occurs. A shorter MTTD indicates that monitoring tools are effective in identifying security incidents promptly. Organizations should strive to minimize MTTD by implementing real-time monitoring tools, automating security assessments, and continuously updating their monitoring techniques. Regularly reviewing and analyzing MTTD can help organizations identify areas for improvement and enhance their security monitoring capabilities.
Mean time to respond (MTTR) measures the average time it takes to respond to a security incident from the moment it is detected. A shorter MTTR indicates that incident response processes are efficient and effective. Organizations should strive to minimize MTTR by having a well-defined incident response plan, conducting regular incident response drills, and fostering collaboration between security teams. Regularly reviewing and analyzing MTTR can help organizations identify bottlenecks in their incident response processes and make improvements.
Future Trends in Application Security Monitoring
As cyber threats continue to evolve, the field of application security monitoring is also undergoing significant changes. Emerging technologies and evolving threat landscapes are shaping the future of security monitoring, presenting both challenges and opportunities for organizations. Some of the key trends that are expected to influence the future of application security monitoring include the adoption of artificial intelligence (AI) and machine learning (ML), the rise of DevSecOps, and the increasing importance of cloud security.
Artificial intelligence (AI) and machine learning (ML) are poised to revolutionize application security monitoring by enabling more advanced threat detection and response capabilities. AI and ML algorithms can analyze vast amounts of data to identify patterns and anomalies that may indicate potential security threats. These technologies can also automate the process of threat detection and response, reducing the reliance on manual intervention and improving the efficiency of security monitoring. As AI and ML continue to advance, organizations are expected to increasingly adopt these technologies to enhance their security monitoring capabilities.
The rise of DevSecOps is another significant trend that is shaping the future of application security monitoring. DevSecOps is an extension of DevOps that integrates security practices into the development and operations processes. By incorporating security monitoring into the DevSecOps pipeline, organizations can identify and address security issues early in the development process, ensuring that security is an integral part of the application lifecycle. The adoption of DevSecOps practices is expected to increase as organizations recognize the importance of integrating security into their development workflows.
The increasing importance of cloud security is also influencing the future of application security monitoring. As organizations migrate their applications and data to the cloud, they must address the unique security challenges associated with cloud environments. Cloud security monitoring involves continuously tracking and analyzing cloud-based resources, detecting potential threats, and ensuring compliance with cloud security best practices. As cloud adoption continues to grow, organizations are expected to invest in advanced cloud network security monitoring tools and techniques to protect their digital assets.
Conclusion
In conclusion, mastering application security monitoring is essential for protecting your organization’s digital assets in today’s increasingly digital world. By understanding the importance of application security, implementing effective monitoring practices, and staying informed about emerging trends, organizations can enhance their security posture and safeguard their applications from potential threats. By taking a proactive and adaptive approach to security monitoring, organizations can stay ahead of evolving threats, ensure compliance with industry standards, and maintain the trust of their users.
