In today’s society it is also crucial to safeguard your network from antagonization on the world wide web. A network vulnerability assessment is the assessment of threats, the identification of current vulnerabilities, and presentation of valuable data to shore up your company’s network. Network vulnerability assessment is, therefore, considered as a technique of identification and quantification of threats in all the devices accessible to the network. This guide is designed to address questions of why, when and how to do IT security assessments.
What do network vulnerability assessments look for?
In an attempt to enhance network security, network vulnerability assessments look for risks and weaknesses in applications and network infrastructure. These specialized tools look into things like unpatched operating systems and software, open ports and services, unprotected wireless networks, incorrect web or network application configurations, network architecture flaws, security policy compliance, mobile device vulnerabilities, access control and permissions, physical security issues, exposed Internet of Things (IoT) devices, weak passwords, and application-level vulnerabilities:
- Unpatched software and operating systems:
Such are among the key causes of network insecurity. These vulnerabilities allow the hacker to perform a hacker’s attack and reach out to thereby acquiring private info. - Open ports and services:
Since attackers can freely use the open ports, they can bypass all the security mechanisms installed and directly access the network systems. Such investigation reveals potential access points for the accessing intruder, whether in the form of open ports or services. - Unsecured wireless networks:
Open wireless networks are always common routes through which the attackers or unauthorized persons launch an attack or unauthorized access to other people’s information. - Misconfigurations in networks or web applications:
One having a wrong installation of a network or failure in web applications could create openings that hackers would exploit. Two examples of the misconfiguration are unsafe SSL/TLS configurations and improper firewall configuration. - The network architecture’s shortcomings include:
I learned that apart from the identification of specific vulnerabilities, meaningful insights into potential complicated failure modes or insufficient segmentation or isolation to prevent lateral movement may only be achievable, if at all, when assessing the overall network architecture. - Observance of security regulations:
This means that your business can also be at risk of data loss, hacking, and legal consequences whenever you breach these security allegations. Vulnerability assessments reduce these risks by considering the degree of conformity with security policies. - Access control and permissions:
Supervisory checks of who is accessing or seeking access to programs or data are essential to ensure that only special users or special systems get access to those special programs or data. - Security policy compliance:
Ensuring that the physical connectivity of the equipment on the network is secure is the best way of avoiding cases of tampering or unlawful entry into the network which is very dangerous to the network. - Vulnerable mobile devices:
Possible weaknesses in mobile devices include, outdated operating systems, badly permitted applications, users and their behavior, and risky settings is what is being looked for by a comprehensive assessment of network vulnerability. - Exposed IoT devices:
The weak IoT devices are known to have a severe impact on a company’s security and privacy situation in the most traumatic manner. They could be in danger from many types of attack like ransomware attack, malware attack, SQL injection or SQLite, wardriving attack, denial of service or DoS attack and zero-day attack. - Weak passwords:
This is followed by poor pass wording as a major contributing factor towards network vulnerabilities. Brute force attacks enable the hackers to guess the pathetic passwords and get hold of private data. - Application-level weaknesses:
Application level vulnerabilities can allow hackers to read, write, delete private data, execute a virus or Trojan program, bypass the authorization or authentication controls or perform a denial of service attack. Application level attacks entail the following; buffer overflow attacks, cross site scripting and SQL injection flaw.
Essential steps for conducting vulnerability assessments
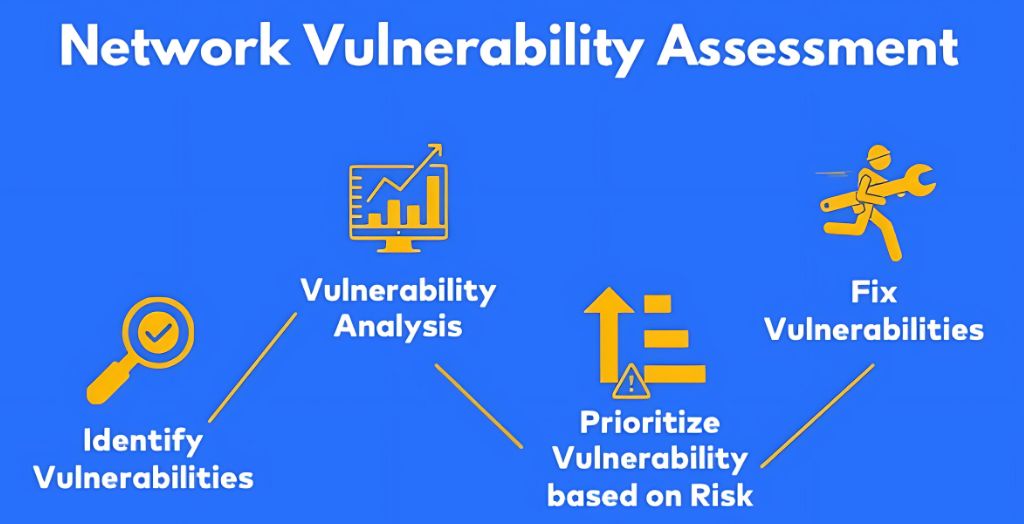
Planning and designing, asset discovery, configuration, network scanning, result analysis, vulnerability prioritization, and report creation are the six crucial processes in the vulnerability assessment process.
- Organizing and creating
Deciding on the precise components and boundaries of the evaluation is the initial step towards the beginning of a network vulnerability assessment. This consists of hardware, user devices, apps and also network infrastructures. After the scope, for each asset specify its security capacities, level of risk, user authorization, settings, configurations and other parameters. Finally, complete any outstanding planning and organizing, equip oneself with all the necessary items that may be needed; organize the test area. - Asset Discovery
The next thing is to choose what should be scanned. Other examples include the allowed use of consortium through corporate owned, personally enabled (COPE) and Bring Your Own Device (BYOD) mobile devices and Internet of Things devices. Secondly, identify the rationale based on which the hardware, apps, devices, and the network element would be assessed. The following ones must be established for these assets: security capabilities, risk tolerance, user permissions, configurations, and others.
- Scanning the network
Scanning is more or less the process of seeking vulnerabilities in your network. A Vulnerability scanner is used in a network to determine possible security risks that are present in a network.
- Analysis of the results
You must examine any issues that are raised after scanning in order to identify any potential weaknesses.
- Prioritizing vulnerabilities
Subsequently in this second process, you can re-sort these new vulnerabilities based on the threat level they represent.
- The creation of reports
Finally, produce an extensive report summarizing the findings of the assessment. Other recommendations that may be taken should also be included in the report as well as a recommendation for further evaluations.
Benefits of network vulnerability assessment for your organization
Regular network vulnerability evaluations can help your company reduce risks, save money, manage patches more effectively, allocate resources more efficiently, and improve continuously.
- Reduction of risks
You then get to know areas that could be exploited and get to minimize exposure mostly reducing the chances of being attacked. By adopting this strategy, you help stop the threats from occurring since you deal with potential problems to computer security before these threats can bend and twist them to their advantage. - Savings
With vulnerability assessments performed to mitigate the risk of data breaches, outages, and other cyber disasters, you might save your company a good deal of money to not have to pay for response, recovery, and legal services. - Improved patch administration
Through such assessments, a business organization can easily address known areas of weakness such as outdated software and configuration that require patching or updating. If your company addresses all the known threats as soon as possible, then you are likely to work in a safer environment. - Resource allocation that is optimized
When you carry out vulnerability assessments you are able to know the best way to use your security resources. It enhances security as it posts the probability of resource and time being allocated to the most vulnerable sectors. - Constant enhancement
Assessments of network vulnerabilities are continuous procedures rather than one-time events. Assessments provide a consistent development of cybersecurity enhancement that extend their operations to accommodate new threats and discoveries made in technology.
The Difference Between Vulnerability Scanning and Vulnerability Assessment

There is one known as vulnerability scanning which has the ability to identify potential weakness in the operating software and systems. The impact and criticality of the vulnerability together with its correlates, the strategies for leveraging the vulnerability are not stated.
On the other hand, the vulnerability assessment methodology is a rather time-consuming method which searches, categorizes and rankings the software and system vulnerabilities. It does offer details on the vulnerability’s impact, seriousness, and potential for exploitation.
An essential component of vulnerability assessment is vulnerability scanning. On its own, though, it is insufficient. Manual analysis is also necessary for vulnerability assessment in order to find and rank vulnerabilities.
Conclusion
Any organization’s security posture and a thorough vulnerability management strategy must include network vulnerability evaluations. You may defend your company against a variety of threats by locating and fixing weaknesses. A network vulnerability assessment can be carried out in a variety of methods, and the optimal strategy will change based on your organization’s unique requirements.
You can keep one step ahead of attackers and resolve security issues before they become major ones by evaluating networks for vulnerabilities and taking action to repair them. In the end, vulnerability assessment of network gives you the chance to improve the dependability and performance of your network.
