As we step into 2025, the digital landscape continues to evolve, bringing new opportunities yet escalating cyber threats. Ensuring network security has never been more critical for businesses of all sizes. The right tools can make a significant difference in protecting sensitive data and maintaining customer trust. In this article, we explore the top 10 essential network security tools that will empower your organization to withstand potential breaches and safeguard your assets. From advanced firewalls to cutting-edge intrusion detection systems, these tools not only enhance your security posture but also help streamline operations in an increasingly complex threat environment. Equip your business with the knowledge and resources required to combat cybercriminals effectively. Dive in and discover how these essential tools can elevate your network security strategy to new heights in 2025!
Importance of Network Security Tools for Businesses
In an era where digital transformation is pivotal for business success, network security has become an indispensable aspect of organizational resilience. With cyber threats growing in sophistication and frequency, businesses are compelled to adopt robust security measures to protect their digital assets. The significance of network security tools cannot be overstated, as they serve as the first line of defense against potential breaches, ensuring that sensitive data remains secure and business operations are not disrupted. Effective network security tools not only protect against external threats but also identify and mitigate internal vulnerabilities, providing a comprehensive security posture.
Moreover, the financial implications of cyber-attacks can be devastating for businesses. The costs associated with data breaches, including regulatory fines, legal fees, and loss of customer trust, can cripple even the most established organizations. By investing in advanced network security tools, businesses can mitigate these risks and safeguard their financial stability. Additionally, the reputational damage caused by a security incident can have long-lasting effects, making it imperative for businesses to demonstrate a strong commitment to protecting customer information and maintaining a secure network environment.
As we move forward into 2025, the threat landscape is expected to become even more challenging, with cybercriminals employing advanced tactics to infiltrate networks. To stay ahead of these evolving threats, businesses must continuously update and enhance their security measures. This involves not only deploying the latest security tools but also fostering a culture of security awareness within the organization. By prioritizing network security and leveraging the right tools, businesses can create a resilient defense strategy that adapts to the ever-changing cyber threat landscape, ensuring long-term success and stability.
Overview of the Top 10 Essential Network Security Tools
In the quest to fortify network defenses, businesses must equip themselves with a diverse array of security tools, each serving a unique purpose in the overall security strategy. The top 10 essential network security tools for 2025 encompass a range of technologies designed to detect, prevent, and respond to cyber threats. From firewalls that act as gatekeepers to intrusion detection systems that monitor network traffic, these tools provide comprehensive protection against a multitude of threats. By understanding the specific functions and benefits of each tool, businesses can make informed decisions about their security investments.
The integration of these tools into a cohesive security framework is crucial for maximizing their effectiveness. While each tool offers distinct capabilities, their combined use creates a multi-layered defense strategy that addresses various aspects of network security. For instance, firewalls and VPNs work together to control access and secure data transmission, while SIEM systems and DLP solutions provide real-time user monitoring and data protection. This holistic approach ensures that no single point of failure exists within the network, enhancing the overall security posture.
As we delve into the specifics of each tool, it is important to recognize that the effectiveness of these tools hinges on proper implementation and ongoing management. Regular updates, configuration adjustments, and continuous monitoring are essential to maintaining optimal performance and adapting to new threats. By adopting a proactive approach to network security and leveraging the capabilities of these essential tools, businesses can create a robust defense mechanism that evolves with the changing threat landscape and provides enduring protection.
Tool 1: Firewall Solutions
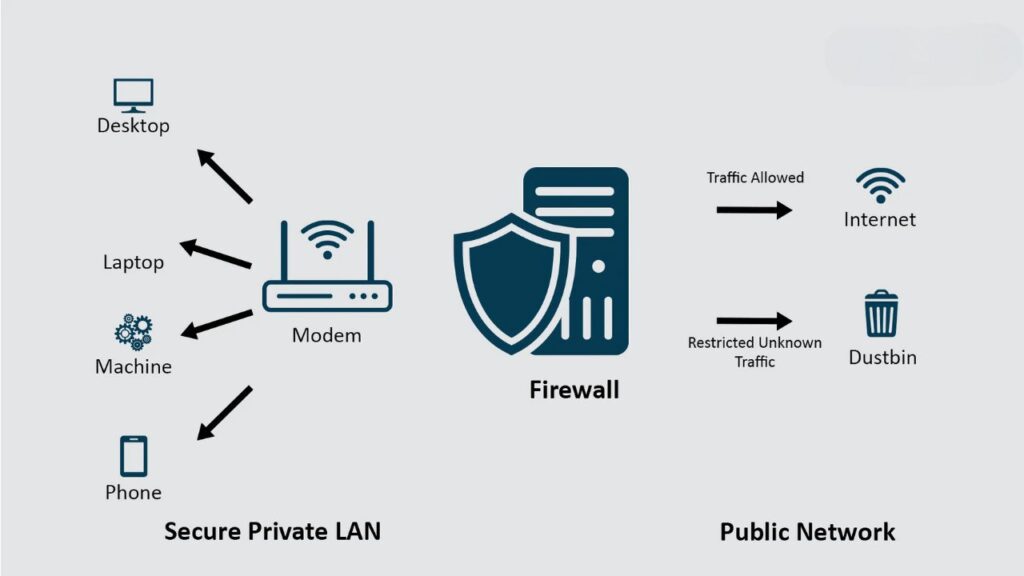
Firewalls are the cornerstone of network security, acting as the first line of defense by controlling incoming and outgoing traffic based on predetermined security rules. In 2025, advanced firewall solutions are more critical than ever, offering features such as deep packet inspection, application awareness, and integrated threat intelligence. These capabilities enable firewalls to detect and block sophisticated threats that traditional firewalls might miss. By implementing state-of-the-art firewall solutions, businesses can ensure that only legitimate traffic is allowed, minimizing the risk of unauthorized access and data breaches.
One of the key advancements in firewall technology is the integration of artificial intelligence (AI) and machine learning (ML) algorithms. These technologies enhance the firewall’s ability to identify and respond to emerging threats in real-time. By analyzing network traffic patterns and identifying anomalies, AI-powered firewalls can proactively block malicious activities before they cause harm. Additionally, the use of threat intelligence feeds allows firewalls to stay updated with the latest threat information, providing a dynamic defense against evolving cyber threats.
The deployment of next-generation firewalls (NGFWs) also offers significant advantages for businesses. NGFWs combine traditional firewall capabilities with additional security functions such as intrusion prevention, antivirus, and content filtering. This convergence of features simplifies security management and provides comprehensive protection against a wide range of threats. By leveraging NGFWs, businesses can achieve a higher level of security while reducing the complexity and cost associated with managing multiple security solutions.
Tool 2: Intrusion Detection and Prevention Systems (IDPS)
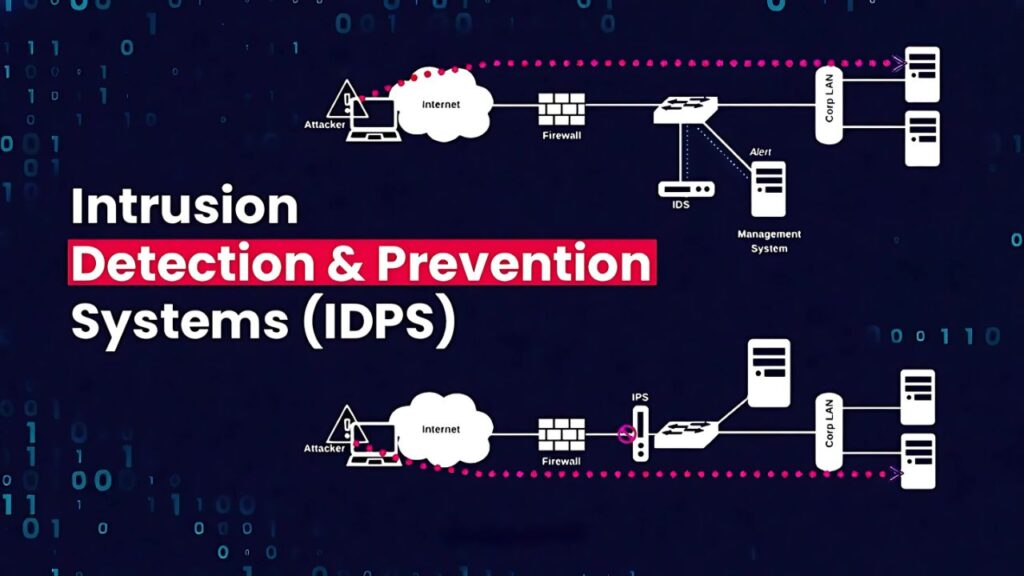
Intrusion Detection and Prevention Systems (IDPS) are essential tools for identifying and mitigating unauthorized activities within a network. These systems work by continuously monitoring network traffic for signs of malicious behavior, such as unusual data transfers or unauthorized access attempts. When a potential threat is detected, IDPS can take immediate action to block the activity and alert security personnel. This proactive approach helps prevent breaches before they can cause significant damage, making IDPS a crucial component of any comprehensive security strategy.
The effectiveness of IDPS has been significantly enhanced by the incorporation of AI and ML technologies. These advancements enable IDPS to analyze vast amounts of data and identify patterns that may indicate a security threat. By learning from past incidents and adapting to new attack techniques, AI-powered IDPS can provide more accurate and timely threat detection. Furthermore, the integration of behavioral analysis allows these systems to distinguish between legitimate user activity and potential threats, reducing the number of false positives and ensuring that security resources are focused on genuine risks.
Another important feature of modern IDPS is their ability to integrate with other security tools and systems. For example, IDPS can work in conjunction with SIEM solutions to provide a holistic view of network security. By correlating data from multiple sources, these integrated systems can identify complex attack patterns that might go unnoticed by standalone tools. This collaborative approach enhances the overall effectiveness of the security infrastructure, providing businesses with a more robust defense against sophisticated cyber threats.
Tool 3: Antivirus and Anti-malware Software

Antivirus and anti-malware software are fundamental components of any network security strategy, providing essential protection against a wide range of malicious software. These tools work by scanning files and programs for known malware signatures and suspicious behavior, preventing infections that could compromise the integrity and confidentiality of business data. In 2025, the capabilities of antivirus and anti-malware solutions will be significantly enhanced through the use of AI and ML technologies, enabling more effective detection and removal of advanced threats.
One of the key advancements in antivirus and anti-malware software is the shift towards behavior-based detection. Traditional signature-based detection methods are limited in their ability to identify new or unknown malware. By analyzing the behavior of programs and files, modern solutions can detect and block zero-day threats that have not yet been cataloged in signature databases. This proactive approach ensures that businesses are protected against the latest malware variants, reducing the risk of infection and data loss.
Another important feature of contemporary antivirus and anti-malware software is the ability to provide real-time protection. By continuously monitoring system activity and network traffic, these tools can detect and respond to threats as they occur. This real-time capability is crucial for preventing the spread of malware within a network and minimizing the impact of an infection. Additionally, the integration of cloud-based threat intelligence allows these solutions to stay updated with the latest threat information, ensuring that businesses are protected against the most recent attacks.
Tool 4: Virtual Private Networks (VPNs)

Virtual Private Networks (VPNs) are essential tools for ensuring secure remote access to a business’s network. By encrypting data transmitted over the internet, VPNs protect sensitive information from interception by unauthorized parties. This is particularly important in today’s increasingly remote and mobile workforce, where employees need to access corporate resources from various locations. In 2025, VPN technology has evolved to provide even greater security and performance, making it an indispensable component of network security strategies.
One of the key advancements in VPN technology is the introduction of next-generation encryption protocols. These protocols, such as WireGuard and Quantum-safe encryption, offer improved security and efficiency compared to traditional VPN protocols. By leveraging these advanced encryption methods, businesses can ensure that their data remains secure during transmission, even in the face of emerging threats. Additionally, the use of AI and ML in VPNs allows for dynamic adjustment of encryption settings, optimizing performance while maintaining robust security.
Another important feature of modern VPNs is the ability to support multi-factor authentication (MFA). By requiring users to provide multiple forms of verification, such as passwords and biometric data, MFA adds an additional layer of security to remote access. This reduces the risk of unauthorized access, even if login credentials are compromised. Furthermore, the integration of VPNs with other security tools, such as firewalls and SIEM systems, enhances the overall security posture by providing comprehensive protection for remote connections.
Tool 5: Security Information and Event Management (SIEM)

Security Information and Event Management (SIEM) systems are vital tools for managing and analyzing security data across an organization’s network. By collecting and correlating data from various sources, SIEM systems provide a comprehensive view of network activity, enabling businesses to detect and respond to security incidents more effectively. In 2025, the capabilities of SIEM systems will be significantly enhanced through the use of AI and ML technologies, allowing for more accurate threat detection and streamlined incident response.
One of the key benefits of modern SIEM systems is their ability to provide real-time monitoring and analysis of security events. By continuously collecting data from network devices, applications, and user activities, SIEM systems can identify potential threats as they occur. This real-time capability is crucial for minimizing the impact of security incidents and preventing data breaches. Additionally, the use of AI and ML in SIEM systems allows for advanced threat detection, as these technologies can identify patterns and anomalies that may indicate a security threat.
Another important feature of contemporary SIEM systems is their ability to integrate with other security tools and platforms. By correlating data from multiple sources, SIEM systems provide a holistic view of network security, enabling businesses to identify complex attack patterns and respond more effectively. This integration also simplifies security management by providing a centralized platform for monitoring and responding to security incidents. Furthermore, the use of automated response capabilities in SIEM systems allows for faster and more efficient incident resolution, reducing the overall impact of security threats.
Tool 6: Data Loss Prevention (DLP) Solutions

Data Loss Prevention (DLP) solutions are essential tools for protecting sensitive information from unauthorized access and exfiltration. These tools work by monitoring and controlling data transfers within and outside the network, ensuring that confidential information remains secure. In 2025, DLP solutions have evolved to provide more comprehensive protection, leveraging AI and ML technologies to detect and prevent data breaches more effectively. By implementing advanced DLP solutions, businesses can safeguard their valuable data and maintain compliance with regulatory requirements.
One of the key advancements in DLP technology is the ability to provide content-aware protection. Traditional DLP solutions rely on predefined rules and patterns to identify sensitive data, which can result in false positives and missed detections. By using AI and ML to analyze the content and context of data transfers, modern DLP solutions can more accurately identify and protect sensitive information. This ensures that businesses can prevent data breaches without disrupting legitimate business activities.
Another important feature of contemporary DLP solutions is the ability to provide real-time monitoring and response. By continuously monitoring data transfers and user activities, DLP solutions can detect and respond to potential threats as they occur. This real-time capability is crucial for preventing data breaches and minimizing the impact of security incidents. Additionally, the integration of DLP solutions with other security tools, such as SIEM systems and firewalls, enhances the overall security posture by providing comprehensive protection for sensitive data.
Conclusion: Choosing the Right Network Security Tools for Your Business
In conclusion, the top 10 essential network security tools for 2025 provide businesses with the comprehensive protection needed to safeguard their digital assets in an increasingly complex threat environment. From advanced firewalls and IDPS to cutting-edge antivirus software and VPNs, these tools offer a multi-layered defense strategy that addresses various aspects of network security. By understanding the specific functions and benefits of each tool, businesses can make informed decisions about their security investments and create a robust defense mechanism that evolves with the changing threat landscape.
Choosing the right network security tools for your business involves considering several factors, including the size and complexity of your network, the nature of your business operations, and the specific threats you face. It is also important to consider the integration capabilities of these tools, as a cohesive security framework is crucial for maximizing their effectiveness. By adopting a proactive approach to network security and leveraging the capabilities of these essential tools, businesses can create a resilient defense strategy that ensures long-term success and stability.
Ultimately, the effectiveness of these tools hinges on proper implementation and ongoing management. Regular updates, configuration adjustments, and continuous monitoring are essential to maintaining optimal performance and adapting to new threats. By prioritizing network security and fostering a culture of security awareness within the organization, businesses can stay ahead of evolving cyber threats and protect their valuable digital assets. Equip your business with the knowledge and resources required to combat cybercriminals effectively, and elevate your network security strategy to new heights in 2025.

