Cybersecurity incidents are frequent and they impact organizations daily. While some data breaches are minor, others can result in substantial financial or data losses. This requires business managers to review their current setups to ensure all necessary precautions are taken.
Network security monitoring is one of the key elements for protecting organizational assets. It’s a process that analyzes network devices and traffic for potential weaknesses and threats. Let’s dive deeper into network security monitoring’s importance, tools, and best practices.
Network security monitoring (NSM)
Network Security Monitoring or NSM is the process of capturing, analyzing and subsequently the processing of network information with the purpose of identifying threats. It involves the act of patient surveillance of the network and logs and events and traffic searching for a forbidden activity on the network. NSM is an essential part of an organization’s comprehensive cybersecurity system since it allows the identification and subsequent prevention of both recognized vulnerabilities and new threats in real-time.
The purpose of NSM is therefore to protect the Confidentiality, Integrity and Availability of the network resources. This is made possible by the use of IDS, packet analyzers and computational intelligence using AI and ML. Such systems assist in achieving these goals through pattern recognition, defining how normal behaviors look like and recognizing when system behaviors are abnormal and may indicate malicious actions.
It also plays a great role in incident response and forensic investigations, thus allowing NSM to give logs or reports on the activities that may take place on the various networks. Attribution, analysis of the scale of an attack, and identification of countermeasures are made possible thanks to these insights by security teams.
Consequently, understanding NSM, its components and main aspects becomes crucial to secure today’s network landscapes and manage threats incoming to modern organizations.
Key components of Network Security Monitoring
In the current security landscape, ongoing network monitoring can give your organization higher visibility. Often, this is a much-needed boost to level the playing field-defending against threats without knowing they exist is much harder. Continuous network security monitoring is essential to a successful cybersecurity strategy.
However, constructing an effective continuous monitoring plan is far from straightforward. It involves various complex elements to be taken into account.
- Determine which data needs to be secured
Given time, resource, and budget constraints, prioritization is vital. The key data and infrastructure must have appropriate security measures and monitoring software.
In a sense, security measures must match the specific risks and threats your organization is exposed to. Appropriate network monitoring tools help to pave the way for more aligned controls.
- Establish an amendment plan for security flaws
While continuous network security and monitoring helps keep the pulse on the current situation, it needs to be complemented by other security measures and best practices. Potential weak points should be closely monitored across the whole network, while sensitive information exchanges should happen over encrypted traffic sessions. However, it’s also necessary to have an action plan to address discovered weaknesses.
It’s a mutually beneficial relationship: monitoring provides the context and information needed to know how the incident response plan should be handled. This positively affects security and network performance, making it easier to address emerging threats.
- Maintain constant endpoint surveillance
Modern organizations have embraced remote-friendly setups, so many endpoints can connect to internal networks. At the same time, endpoints need to be closely monitored as each can access confidential information. This applies to all desktops, servers, and similar devices (multi-factor authentication should also be encouraged).
If an employee unintentionally endangers the network, it’s important to pinpoint which endpoint was affected quickly. A timely reaction using monitoring software can help mitigate risks quickly. Conversely, prolonged malware presence heightens the risk of much bigger problems.
- Recognize abnormal user behavior
Continuous network monitoring provides much information on how users act. This helps to establish typical user patterns within your organization, especially focusing on their interaction with the network’s applications and data.
Normally, employees follow similar usage habits on a day-to-day basis. Hence, deviations from these norms can be indicative of security violations. Sensitive resources should be monitored even more attentively to prevent potential risks before they escalate into actual problems.
- Perform third-party monitoring
Securing an internal network is paramount for an organization’s security. However, watching the third parties you work closely with is also important. Threats from third-party partners shouldn’t be underestimated—if they get breached, this may also cause danger to your systems.
Third-party vendor security also has strict vendor requirements in terms of compliance. This means that organizations’ security status, as well as compliance, will have to align with third-party partners, as well. Implementing various boundaries and access checks with monitoring software will help establish a functioning system for collaborating with third parties.
Network Security Monitoring: Protection from Exploits and Attacks
As previously mentioned, network security monitoring exists to help organizations discover, locate, and mitigate network intrusions. It does this by analyzing various elements within your network, including:
- Client-server communications: Traffic that involves requests for service made by users to servers on a network
- Encrypted traffic sessions: Encoded data sent and received through the network
- Network payload: Data sent and received in network packets
- Network protocols: The rules that determine how data is transmitted on the network
- Traffic flow: Sequences of packets carrying information between multiple endpoints
- Traffic patterns: Normal, expected network traffic patterns and any abnormal deviations that may indicate a breach
Network security monitoring is the practice that takes into account your organization’s security structure; this approach entails capturing network traffic, comparing this to expected standard then assessing variations for any possibly abusive or dodgy events. In the event of a possible breach, Network security monitoring also gives alerts/notifications at the appropriate time.
Benefits of Network Security Monitoring
As the city of Troy discovered so long ago, no outer defense is impregnable.
Regardless of how well you fortify network access, at some point, a threat actor will find a way inside. How much damage they do and what it will cost your organization depend heavily on how quickly you can take action. Data breach costs climb significantly the longer an attacker is allowed to remain in the network. A study recently conducted showed that the average organization which experiences a data breach with a lifecycle more than 200 days ends up $1.12 million poorer than one where the lifecycle of the data breach is less than 200 days.
Therefore, the effectiveness of any network security monitoring solution depends on transparency. Overlooking network security puts your critical applications in the crosshairs, helping you identify, analyze, and mitigate nasty traffic, verify unusual traffic, pinpoint specific and generic threats, and address security breaches more effectively. In other words, you get the levels of perception that you want to be able to recognize the risks that may well escalate if not handled appropriately.
Automated monitoring solutions built on real-time visibility allow administrators to see the big picture, accurately visualizing the movement of traffic and data across the network. This carries with it certain key advantages:
- Minimizing response times
Perhaps the most direct benefit of network security monitoring is that it reduces the time needed to locate, evaluate, and respond to security threats within your network. It does this not only through increased real-time tracking of all network activity but also by automating monitoring tasks.
- Improved customer experience
Your business isn’t the only victim when you experience a security breach; the customers who depend on your networks to provide essential services also suffer. Network security monitoring helps ensure that threats to these services are resolved quickly, creating a better, more consistent customer user experience.
- Enhanced efficiency
Traditional network monitoring security is more than a full-time job, demanding near-constant attention from IT teams and network administrators. Modern network security tools automate many of these responsibilities. As a result, valuable IT professionals can make more efficient and productive use of their time while also reducing the likelihood of human error.
- Increased cost savings
In the broad spectrum of using security services, the most apparent advantage is an assurance that your business expends capital on its
network infrastructure monitoring without a high propensity to lose such
an investment to a breach. Thus, these elevated cost reductions are even further magnified when looking at all the various network enhancements that can result from improved network performance visibility.
Features of Network Security Monitoring
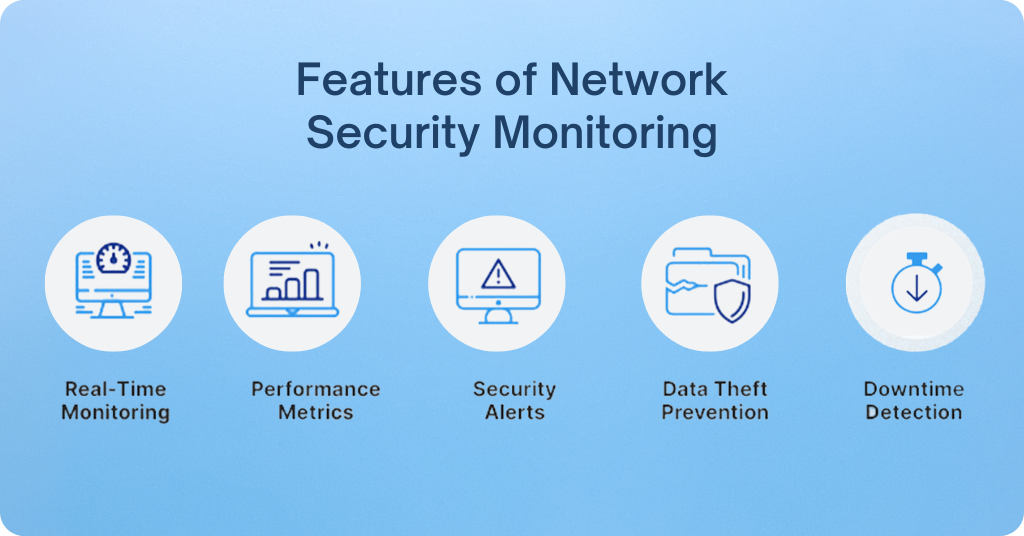
Network Security Monitoring (NSM) is a key security concept in computer networks responsible for the consistent, systematic acquisition, processing, and analysis of network information for the purposes of threat identification and response. Below are five key features of NSM:
- Real-Time Threat Detection
Another advantage of the NSM is the feature that allows for the live watching of network traffic. Usually, NSM tools involve traffic analysis, storage of logs and other types of analysis for performance of patterns, which gives them the ability to determine what is suspicious, such as unauthorized access attempts, frequent data transfers, and malware infections. This form of detection assures that with actual time periods between the time an attack occurred and the time it was detected so much damage is prevented from happening. More sophisticated NSM solutions need IDS and IPS to work as one in order to increase the detection rates.
- Comprehensive Visibility
As with NW wiping, NSM gives a complete picture of the entire network infrastructure. It records traffic from numerous endpoints, gadgets, and applications while guaranteeing that no irregularity as diminutive as it is will be overlooked. Such visibility includes the ability to observe the state of cloud, on-premises servers and IoT devices. The feature is rather valuable as today’s organizations employ intricate and dispersed systems. This way NSM assists in finding the gaps and areas, which may be potentially dangerous for a company and used by the attackers.
- Advanced Analytics and Threat Intelligence
New generation NSM tools based on AI-ML algorithms to analyze networks’ large traffic and provide efficient results. These systems imply establishing prior behaviors so as to provide measure towards which deviants that may point towards threats then find expression. In addition to threat intelligence feeds, the NSM systems offer an approach to detecting known malicious IPs, domains, and file hashes improving the identification of complex and sophisticated operations.
- Incident Response and Forensics
Apart from only detecting suspicious activities, NSM helps in incident response by giving descriptions of the network activities. These logs are rather important for investigations; with their help, the security teams detect the source of the attack, its nature, and its consequences. It also emerges that many NSM systems are equipped with features like notification, response templates and the capability to connect to SIEM for the purpose of enhancing decision making and speed of response.
- Scalability and Automation
As discussed, NSM tools are developed to respond to the complexity of the current environments as the organization grows. From a local network to an international endeavour, NSM systems are completely flexible to assimilate all these points of convergence while not a single endpoint’s performance is compromised. Furthermore, each of the steps has that automation factor whereby things such as alerting, reporting, and the actual mitigation can be done to a large extent with little to no human interaction involved. Automation takes a lot of load off the security teams, increases effectiveness and guarantees constantly vigilant identification of threats, even during periods of increased load and in complex conditions.
Network Security Monitoring Applies to All Monitoring

A new and crucial part of today’s security is Network Security Monitoring or NSM which is defined as all Network Monitoring to an infrastructure. It goes much beyond merely identifying potential cyber threats, and includes a vast amount of monitoring techniques for keeping a network stable, fast, and secure.
With respect to real-time traffic analysis, endpoint activity monitoring, application behavioral analysis and overall cloud and On-Premise solutions, NSM is a functional approach. Their broad approach means that there is no part of the network that an organization can fail to see as an enemy’s target.
Another important principle of NSM is that it can help monitor all aspects of an organization by relating the events that are expressed in tools as logs, PCAPs, or system performance metrics. To this end, any abnormality is detected whether it resulted from a cyber attack or the normal process of conducting business.
For example, NSM could identify unauthorized accessing, abounding use of the bandwidth, those misconfigured systems that could possibly lead to vulnerabilities. Due to timely Identification and monitoring of risks across all layers within the network NSM assures that organizational risks can be averted effectively as efficiency in organizational operations is enhanced.
Also, NSM can easily work with other tools such as an Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM), and threat intelligence platforms. These integrations facilitate NSM to provide analytical information to Incident Response, Computer Forensics, and Compliance groups. Open to almost any depends on the complexity of the network architectures – local, hybrid or fully cloud environments proves that it is a versatile system.
NSM is the infrastructure in all monitoring activities and integrates network management security. It also affords organizations constant control and timely threat alert, which enables the organization to protect and secure their networks, manage their resources and remain relevant against the new emerging threats.
Conclusion
A key to enhanced security, reliability and performance monitoring of an organization’s information technology system is through network monitoring. In this way, it analyzes the network traffic and device behavior, and recognizes the threats and improvement for its functionality and security. Contemporary tools use computer sciences, automation, and operational data to add high visibility in network activities and opportunities to respond rapidly to issues.
Incidents which have happened with various organizations prove this proposition that in a technologically advanced world where even the complexity of cyber attacks are rising, networking has become not only a technical marvel but also a strategic workforce. When integrated with solutions, such as SIEM or the Threat Intelligence system, it greatly improves an organization’s capabilities in protection, identification of threats, and response to those threats. Besides security, it makes a network run smoothly and as a result organizations are able to provide their services without any hindrance.
Thus, Split Point Solutions can protect important information, improve system efficiency, and develop defenses against new generation cyber threats by investing in proper approach to network monitoring.